Revolutionizing Physical Security for the Modern Era
In today’s rapidly evolving security landscape, Physical Security as a Service (PhySaaS) is emerging as a game-changer for businesses seeking comprehensive protection. PhySaaS offers a fully managed, hybrid cloud-based security platform that integrates cutting-edge technologies to safeguard people, assets, and facilities.
What is PhySaaS?
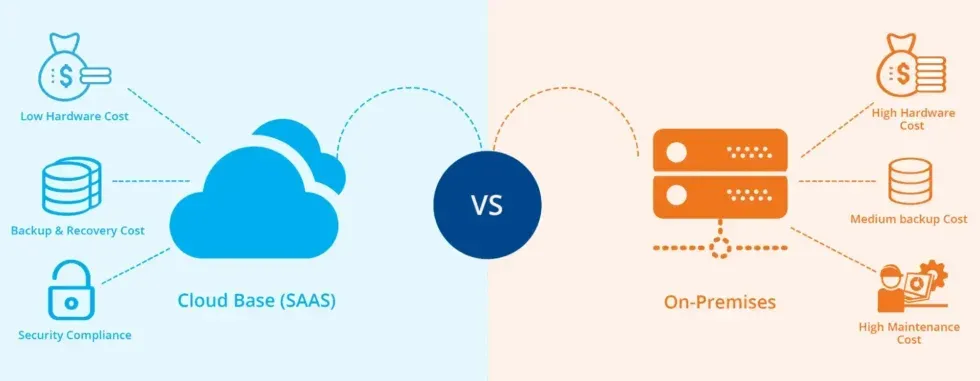
PhySaaS is an innovative approach to physical security that combines video surveillance, access control, environmental monitoring, and more into a single, unified platform. This cloud-based solution eliminates the need for traditional hardware like NVRs, DVRs, and on-premises servers, replacing them with a more flexible and scalable system.
Key Components of PhySaaS
• Video Security: High-quality cameras with onboard processing and storage capabilities.
• Access Control: Seamlessly integrated systems for managing entry points.
• Environmental Monitoring: Sensors for air quality, temperature, and other environmental factors.
• Alarm Systems: 24/7 professional monitoring and intrusion detection.
• Visitor Management: Streamlined check-in processes integrated with other security features.
Benefits of PhySaaS over Traditional Security Systems
• Cost-Effectiveness: PhySaaS operates on a monthly recurring charge (MRC) plan, transforming large capital expenditures into manageable operational costs. This model eliminates upfront hardware investments and reduces maintenance expenses.
• Enhanced Security and Monitoring: PhySaaS leverages AI for proactive protection and real-time threat detection and response, significantly improving overall security posture.
• Scalability and Flexibility: Unlike traditional systems requiring physical upgrades, PhySaaS easily scales to accommodate multiple locations and adapt to changing security needs.
• Remote Management and Accessibility: PhySaaS provides a centralized interface for managing all security aspects remotely, enabling security teams to monitor and respond to incidents from anywhere, at any time, using any device.
• Automatic Updates and Future-Proofing: Customers benefit from automatic software updates, ensuring the security system remains cutting-edge without manual upgrades or hardware replacements.
• Comprehensive Integration: PhySaaS offers seamless integration of various security components, providing a more cohesive and effective security strategy compared to disparate traditional systems.
Tips for Transitioning to PhySaaS
• For First-Time Buyers:
• Assess Your Needs: Carefully evaluate your current security requirements and future growth plans. Identify key areas needing improvement.
• Start Small: Consider piloting PhySaaS in a specific area or location before a full-scale deployment.
• Prioritize Integration: Ensure the PhySaaS solution integrates with your existing IT infrastructure and other business systems.
• Understand the MRC Model: Familiarize yourself with the monthly recurring charge (MRC) model and factor it into your budget.
• Gradually Replacing Traditional Security Solutions:
• Phased Rollout: Implement PhySaaS in phases, replacing outdated components of your traditional system one at a time.
• Hybrid Approach: Run PhySaaS alongside your existing system during the transition period to ensure continuous security coverage.
• Data Migration: Plan for a smooth data migration process to transfer historical security data to the PhySaaS platform.
• Training and Support: Provide adequate training and support to your security team to ensure they can effectively use the new system.
Final Thoughts
Revolutionizing Physical Security for the Modern Era
In today’s rapidly evolving security landscape, Physical Security as a Service (PhySaaS) is emerging as a game-changer for businesses seeking comprehensive protection. PhySaaS offers a fully managed, hybrid cloud-based security platform that integrates cutting-edge technologies to safeguard people, assets, and facilities.
What is PhySaaS?
PhySaaS is an innovative approach to physical security that combines video surveillance, access control, environmental monitoring, and more into a single, unified platform. This cloud-based solution eliminates the need for traditional hardware like NVRs, DVRs, and on-premises servers, replacing them with a more flexible and scalable system.
Key Components of PhySaaS
• Video Security: High-quality cameras with onboard processing and storage capabilities.
• Access Control: Seamlessly integrated systems for managing entry points.
• Environmental Monitoring: Sensors for air quality, temperature, and other environmental factors.
• Alarm Systems: 24/7 professional monitoring and intrusion detection.
• Visitor Management: Streamlined check-in processes integrated with other security features.
Benefits of PhySaaS over Traditional Security Systems
• Cost-Effectiveness: PhySaaS operates on a monthly recurring charge (MRC) plan, transforming large capital expenditures into manageable operational costs. This model eliminates upfront hardware investments and reduces maintenance expenses.
• Enhanced Security and Monitoring: PhySaaS leverages AI for proactive protection and real-time threat detection and response, significantly improving overall security posture.
• Scalability and Flexibility: Unlike traditional systems requiring physical upgrades, PhySaaS easily scales to accommodate multiple locations and adapt to changing security needs.
• Remote Management and Accessibility: PhySaaS provides a centralized interface for managing all security aspects remotely, enabling security teams to monitor and respond to incidents from anywhere, at any time, using any device.
• Automatic Updates and Future-Proofing: Customers benefit from automatic software updates, ensuring the security system remains cutting-edge without manual upgrades or hardware replacements.
• Comprehensive Integration: PhySaaS offers seamless integration of various security components, providing a more cohesive and effective security strategy compared to disparate traditional systems.
Tips for Transitioning to PhySaaS
• For First-Time Buyers:
• Assess Your Needs: Carefully evaluate your current security requirements and future growth plans. Identify key areas needing improvement.
• Start Small: Consider piloting PhySaaS in a specific area or location before a full-scale deployment.
• Prioritize Integration: Ensure the PhySaaS solution integrates with your existing IT infrastructure and other business systems.
• Understand the MRC Model: Familiarize yourself with the monthly recurring charge (MRC) model and factor it into your budget.
• Gradually Replacing Traditional Security Solutions:
• Phased Rollout: Implement PhySaaS in phases, replacing outdated components of your traditional system one at a time.
• Hybrid Approach: Run PhySaaS alongside your existing system during the transition period to ensure continuous security coverage.
• Data Migration: Plan for a smooth data migration process to transfer historical security data to the PhySaaS platform.
• Training and Support: Provide adequate training and support to your security team to ensure they can effectively use the new system.
Final Thoughts
PhySaaS represents a significant leap forward in physical security technology. By offering a fully managed, cloud-based solution, it addresses many of the limitations of traditional security systems. For businesses looking to enhance their security measures while optimizing costs and operational efficiency, PhySaaS presents a compelling and future-ready option. As the security landscape continues to evolve, PhySaaS stands at the forefront, ready to meet the challenges of tomorrow’s security needs.
Case Studies







Blogs











